Governance, compliance, and regulatory frameworks that lay down the guidelines for best practices. Organizations comply with these to ensure they meet regulatory requirements, enhance business processes, improve security, and meet all other objectives. These frameworks ensure that there is a universal language to settle the gap in the tech world from server rooms to strategic boardrooms of the organization. These frameworks aid the various stakeholders of the company including:
organization. These frameworks aid the various stakeholders of the company including:
- Internal auditors and other internal stakeholders can leverage these frameworks to assess the effectiveness of controls within their organization.
- External auditors can utilize these standards to evaluate and verify the controls in place, providing a stamp of approval.
- Other stakeholders like customers and potential investors can gain valuable insights into potential risks when considering partnerships with your organization.
REGULATORY FRAMEWORKS
The following are the most common regulatory frameworks that are part of an Information Security (IS) team.
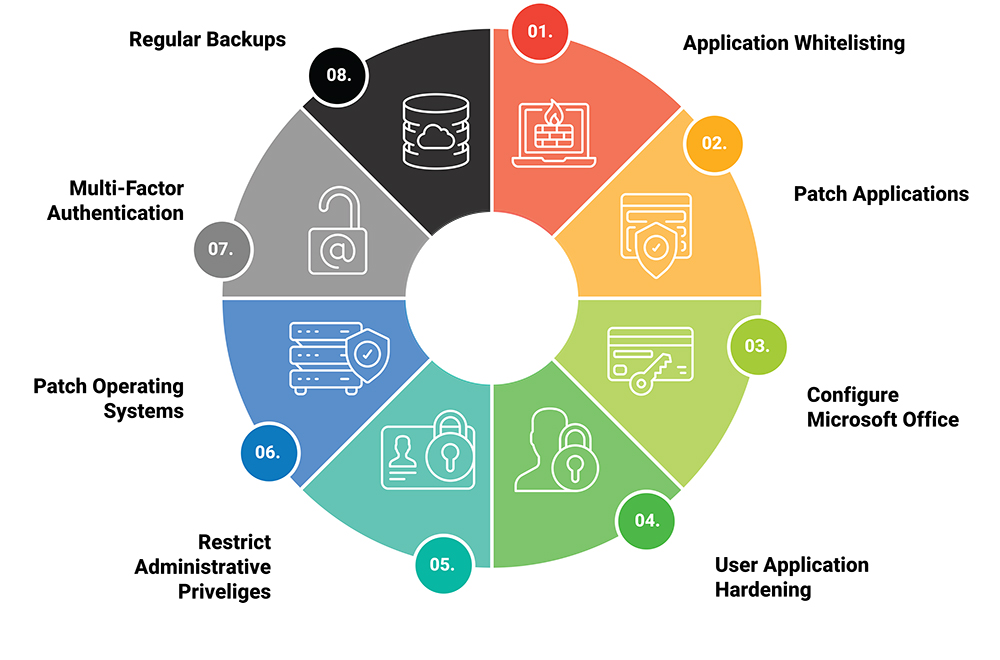
Essential 8 – ACSC
The Australian Cyber Security Centre’s (ACSC) Essential Eight is a critical shield against cyber threats. This free framework outlines eight fundamental actions that increase an organization’s cybersecurity posture. By implementing measures like application patching, multi-factor authentication, and user application hardening, businesses make it much harder for attackers to gain a foothold in their systems. The Essential Eight empowers organizations of all sizes to take a proactive approach to cybersecurity, reducing the risk of data breaches and costly disruptions. These include: Application Control, Patch Applications, Configure Microsoft Office Macro Settings, User Application Hardening, Restrict Administrative Privileges, Patch Operating Systems, Multi-factor Authentication, Regular Backups
NIST
The National Institute of Standards and Technology (NIST) is a federal agency within the Department of Commerce. It mitigates manufacturing, quality control requirements, and security, among other domains. The agency has partnered with security industry experts, other government agencies, and relevant authorities to develop controls to help critical IT infrastructure operators reduce cybersecurity risk.
NIST benefits organizations of all sizes. While large enterprises and government agencies commonly use it, organizations can leverage it to manage cybersecurity risk.

DISP
Australia’s Defense Industry Security Program (DISP) acts as a multi-tiered security vetting system for businesses. Designed to safeguard sensitive information and capabilities, DISP ensures industry partners possess the necessary security protocols to participate in Defense tenders and contracts. The program offers participating entities a valuable suite of benefits, including access to security expertise, risk management guidance, and support services. Ultimately, DISP fosters a collaborative environment where both Defense and industry can operate with confidence.
ISO 27001
ISO/IEC 27001 is the international standard for information security. It sets out the specifications for an effective ISMS (information security management system).
ISO 27001’s best-practice approach helps organizations manage their information security by addressing people, processes, and technology.
Certification to the ISO 27001 standard is recognized worldwide to indicate that your ISMS is aligned with information security best practices.
Part of the ISO 27000 series, ISO 27001 sets out a framework for organizations to establish, implement, operate, monitor, review, maintain, and continually improve an ISMS.


Board Advisory
Cybersecurity is a top business concern. This section equips your board with insights to navigate compliance, governance, and risk. We’ll cover cyber threats, relevant regulations, best practices for governance, fostering a security culture, effective oversight, and valuable resources to keep your board informed for strategic decision-making.
Customer success stories
Whether it be business, government or enterprise level organisations, Yira Yarkiny is here to help! Explore our success stories below.




